IaaS vs PaaS vs SaaS: Their Role in Cloud Strategy
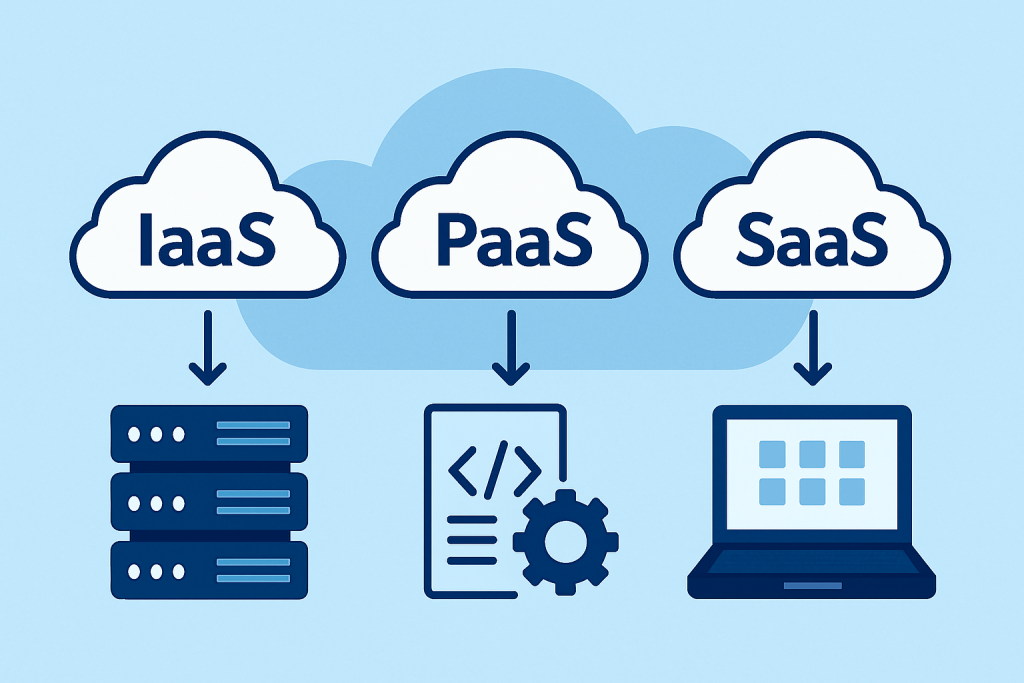
Compute services are no longer working quietly in the background—they are right at the heart of every major business decision. From developing modern applications to managing huge volumes of data or streamlining IT operations, the way you use cloud computing—whether it’s IaaS, PaaS, or SaaS—can shape the success of your entire digital strategy. Let’s break […]
Why Government Projects Need the Right IT Consulting Partner

Walk into a government office, and you will often find a paradox. On the one hand, there are passionate public servants with a vision for a better society—more accessible healthcare, faster legal systems, and transparent governance. On the other hand, these ambitions are tethered to legacy systems, manual workflows, and bureaucratic inertia. Somewhere between intent […]
From Reactive to Proactive: The Modern IT Consultant’s Mindset

Things move fast in the IT world. Businesses are constantly juggling new challenges—whether it is keeping data safe from cyber threats, navigating digital transformation, shifting to the cloud, or figuring out how to use AI in a smart way. With all that going on, relying on a “wait-and-see” approach to IT just does not make […]
Top 5 Signs Your Business Needs IT Consulting

Running a business today means juggling a million things at once—marketing, sales, customer service and then there is your tech stack. If your team is constantly wrestling with slow systems, security scares, or clunky workflows, those aren’t just minor annoyances, they’re red flags. Maybe you’ve brushed it off with “We’ll fix it later,” but here’s […]
When to Hire an IT Consultant vs. Building an In-House IT Team
These days, technology plays a role in almost every part of how businesses operate and grow. Whether it is keeping customer data safe or helping teams collaborate seamlessly, it’s hard to imagine running a business without it. As a result, as your company grows, the question inevitably arises: Should we bring in an IT consultant […]
Cloud Migration in Manufacturing: Transforming Real-Time System

Cloud computing has revolutionized many industries, bringing flexibility, scalability, and cost-effectiveness to the forefront. Yet, one sector has been slower to embrace this shift — manufacturing. The hesitation is not because manufacturers do not understand the benefits, but because they still rely heavily on real-time systems, old equipment, and managing everything on-site. But times are […]
Cloud Migration Mastery: Turning Complexity into Clarity
Achieving cloud migration mastery is crucial for digital transformation—it’s the key to unlocking agility, scalability, and innovation. However, the journey toward the cloud is rarely linear or simple. Instead of a seamless shift, most organizations face unexpected complexity, operational disruptions, and architectural chaos. Even though there is widespread enthusiasm for cloud adoption, enterprises frequently underestimate […]
How to Build a Cloud Migration Strategy for Startups

For startups, agility is a must-have. The ability to pivot quickly, scale fast, and keep innovating gives young businesses a real advantage. Cloud computing plays a big role in making that flexibility possible but jumping into the cloud without a clear plan can lead to unexpected problems. Startups deal with unique challenges: tight resources, fast-moving […]
Emerging Cloud Migration Trends to Watch
Cloud migration is no longer an IT upgrade, it is a business necessity. Businesses worldwide are embracing the cloud to increase productivity, reduce expenses, and stay ahead in today’s more complex digital landscape. Yet as cloud technology gets more advanced, so do the strategies and tools businesses use to move. Cloud migration will be driven […]
Why Docker is Essential for DevOps Pipelines

In the world of DevOps, it is all about getting applications deployed quickly, securely, and efficiently. Consequently, Docker has proven to be very useful, providing developers and operation teams with a consistent environment all through the software development cycle. Moreover, Docker makes it easier to develop, test, and deploy applications by packaging them into containers. […]